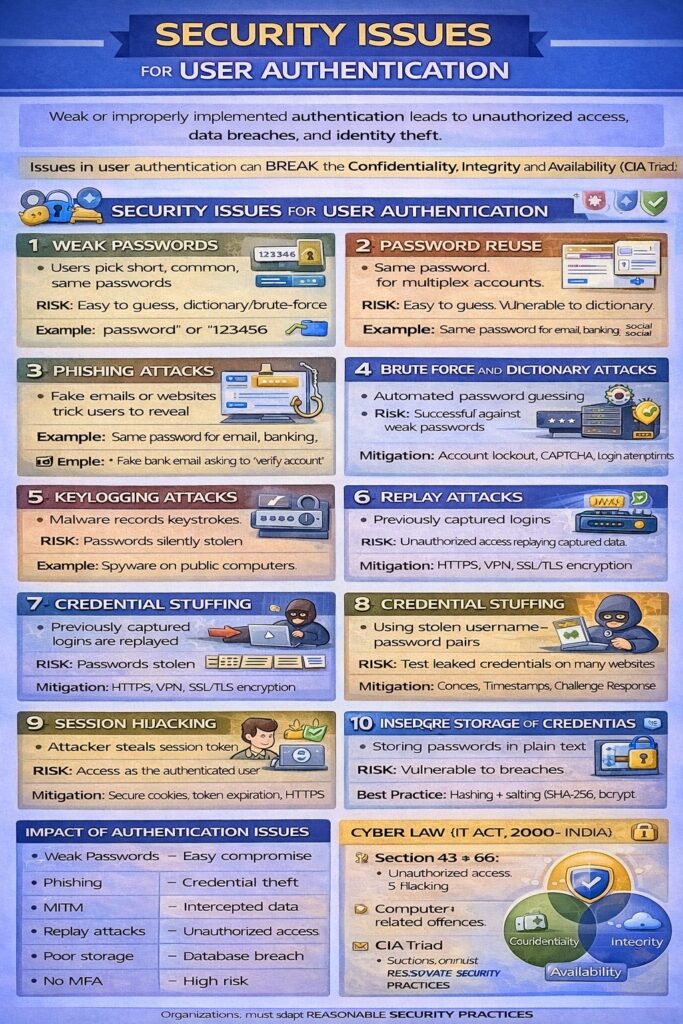
Security Issues for User Authentication
Introduction
User Authentication is the first and most critical line of defense in any information system. It ensures that only legitimate users gain access to system resources. However, authentication mechanisms themselves are exposed to several security issues and attacks.
Weak or improperly implemented authentication can lead to unauthorized access, data breaches, identity theft, and legal consequences under cyber laws.
Major Security Issues in User Authentication
1. Weak Passwords
Description
Users often choose:
- Short passwords
- Common words
- Same password for multiple accounts
Risk
- Easy to guess
- Vulnerable to dictionary and brute-force attacks
Example
Password like 123456 or password
2. Password Reuse
Description
Using the same password across multiple systems.
Risk
- If one system is compromised, all linked accounts are exposed
Example
Same password for email, banking, and social media
3. Phishing Attacks
Description
Attackers trick users into revealing credentials using fake emails or websites.
Risk
- User willingly gives login details
- Difficult to detect
Example
Fake bank email asking to “verify account”
4. Brute Force and Dictionary Attacks
Description
Automated attempts to guess passwords.
Risk
- Successful against weak or short passwords
Mitigation
- Account lockout
- CAPTCHA
- Login attempt limits
5. Keylogging Attacks
Description
Malware records keystrokes to capture passwords.
Risk
- Passwords stolen silently
Example
Spyware installed on public computers
6. Man-in-the-Middle (MITM) Attacks
Description
Attacker intercepts communication between user and server.
Risk
- Credentials captured or altered
Mitigation
- HTTPS
- SSL/TLS encryption
- VPN
7. Replay Attacks
Description
Previously captured authentication data is reused.
Risk
- Unauthorized access without knowing password
Mitigation
- Nonce
- Timestamps
- Challenge–response protocols
8. Credential Stuffing
Description
Using leaked username-password pairs from data breaches.
Risk
- High success rate if users reuse passwords
9. Insecure Storage of Credentials
Description
Passwords stored in:
- Plain text
- Weak encryption
Risk
- Complete compromise if database is breached
Best Practice
- Hashing + Salting (SHA-256, bcrypt)
10. Session Hijacking
Description
Attacker steals session tokens.
Risk
- Bypass authentication
Mitigation
- Secure cookies
- Token expiration
- HTTPS
11. Biometric Authentication Issues
Description
- False Acceptance (FAR)
- False Rejection (FRR)
- Privacy concerns
Risk
- Biometric data cannot be changed once compromised
12. Lack of Multi-Factor Authentication (MFA)
Description
Using only single-factor authentication.
Risk
- Password compromise leads to full access
Solution
- Implement MFA (Password + OTP / Biometrics)
Authentication Security Issues Summary Table
| Issue | Impact |
|---|---|
| Weak passwords | Easy compromise |
| Phishing | Credential theft |
| MITM | Intercepted data |
| Replay attacks | Unauthorized access |
| Poor storage | Database breach |
| No MFA | High risk |
Security Issues and CIA Triad
- Confidentiality → Broken by stolen credentials
- Integrity → Impersonation and data tampering
- Availability → Account lockouts, DoS attacks
Authentication Security Issues & Cyber Law (India)
- IT Act, 2000
- Section 43 → Unauthorized access due to weak security
- Section 66 → Computer-related offences
📌 Organizations must adopt reasonable security practices.
Real-Life Example
Data breach caused by:
- Weak passwords
- No MFA
- Poor credential storage
Result:
- Financial loss
- Legal action
- Loss of user trust
Best Practices to Reduce Authentication Issues
- Enforce strong password policies
- Enable Multi-Factor Authentication
- Use HTTPS and secure channels
- Educate users about phishing
- Regular security audits
- Secure password storage
Conclusion
Security issues in user authentication pose serious threats to information systems. Most breaches occur not due to complex attacks, but due to weak authentication practices. Implementing strong authentication mechanisms, MFA, secure storage, and user awareness is essential to protect systems, users, and organizations.
