Security Functional Requirements
Introduction
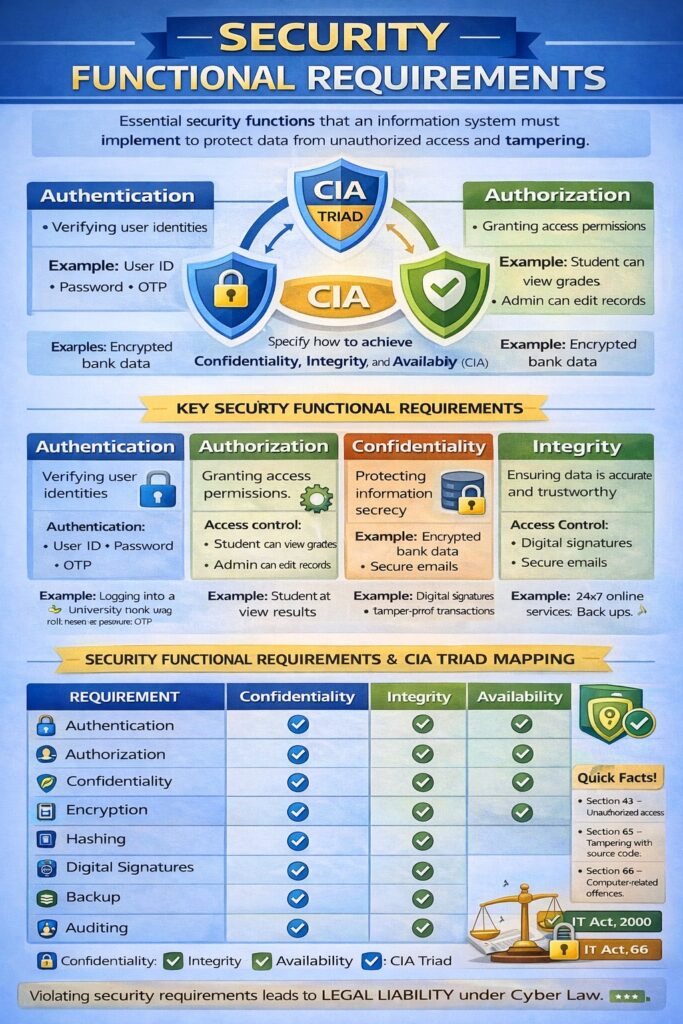
Security Functional Requirements define what a system must do to protect information and resources from security threats. These requirements ensure that an information system enforces confidentiality, integrity, and availability (CIA Triad) in a practical and measurable way.
In simple words:
👉 Security functional requirements specify the security functions a system must provide.
They are crucial in:
- Secure system design
- Risk management
- Cyber law compliance
- Evaluation of trusted systems
Objectives of Security Functional Requirements
- Prevent unauthorized access
- Protect data from modification or destruction
- Ensure accountability and traceability
- Support legal and audit requirements
- Reduce security risks
Major Security Functional Requirements
1. Identification and Authentication
Meaning
- Identification: User claims an identity (User ID)
- Authentication: System verifies that identity
📌 “Who are you?” and “Can you prove it?”
Techniques
- Passwords / PINs
- OTP
- Smart cards
- Biometrics (fingerprint, face recognition)
Example
Logging into a university portal using roll number + password + OTP.
2. Authorization (Access Control)
Meaning
Authorization defines what an authenticated user is allowed to do.
📌 Authentication → Authorization
Access Control Models
- DAC – Discretionary Access Control
- MAC – Mandatory Access Control
- RBAC – Role-Based Access Control
Example
- Student → View results
- Teacher → Upload marks
- Admin → Modify records
3. Confidentiality Requirement
Meaning
Ensures information is not disclosed to unauthorized entities.
Security Mechanisms
- Encryption
- Access control lists (ACL)
- Secure communication (HTTPS, VPN)
Example
Encrypted online banking transactions.
4. Integrity Requirement
Meaning
Ensures that data is not altered illegally or accidentally.
Security Mechanisms
- Hash functions (SHA)
- Digital signatures
- Checksums
- Audit logs
Example
Marks stored in examination database cannot be modified without authorization.
5. Availability Requirement
Meaning
Ensures authorized users have timely access to data and services.
Security Mechanisms
- Backup & recovery
- Redundant servers
- Fault tolerance
- DoS/DDoS protection
Example
ATM services available 24×7.
6. Non-Repudiation
Meaning
Ensures that a user cannot deny performing an action.
Security Mechanisms
- Digital signatures
- Time stamping
- Secure logs
Example
Online agreement signed using digital signature.
7. Accountability and Auditing
Meaning
Ensures all user actions are traceable to a specific individual.
Security Mechanisms
- System logs
- Transaction logs
- Audit trails
📌 Important for cyber crime investigation and legal evidence.
Example
Tracking login attempts and data changes in a banking system.
8. Security Management Requirement
Meaning
Ensures proper management of security controls.
Includes
- User account management
- Password policies
- Patch management
- Security updates
Example
Forced password change every 90 days.
Security Functional Requirements and CIA Mapping
| Requirement | CIA Component |
|---|---|
| Authentication | Confidentiality |
| Authorization | Confidentiality |
| Encryption | Confidentiality |
| Hashing | Integrity |
| Digital Signature | Integrity + Non-repudiation |
| Backup | Availability |
| Auditing | Integrity + Accountability |
Security Functional Requirements in Cyber Law (India)
Under IT Act, 2000:
- Section 43 → Unauthorized access, damage
- Section 65 → Tampering with source code
- Section 66 → Computer-related offences
📌 Lack of security controls can result in legal liability and penalties.
Real-Life Example: Online Banking System
- Authentication → User ID + Password + OTP
- Authorization → User can view only own account
- Confidentiality → Encrypted data
- Integrity → Digital signatures
- Availability → Backup servers
- Auditing → Transaction logs
Advantages of Security Functional Requirements
- Clear security implementation
- Reduced cyber risks
- Legal compliance
- Improved trust
- Easier system evaluation
Conclusion
Security Functional Requirements are the operational backbone of information security. They translate abstract security goals into practical system controls such as authentication, authorization, encryption, auditing, and backup. A system that satisfies these requirements is more secure, reliable, and legally compliant.
